Could Code Signing Have Prevented the CrowdStrike-Microsoft Outage?
By: Ella Schwartz, Vice President of Professional Services
July 29, 2024
On July 19, a massive technology outage brought critical infrastructures worldwide to a
standstill. Flights were grounded, emergency services were disrupted, banking was halted, and
computers running Windows were crashing, displaying the blue screen of death.
What happened?
The issue was triggered by a problematic software update from the cybersecurity company,
CrowdStrike. The company relies on access to computer systems to protect users from hackers
and cyber attackers. The updated code dispatched to machines running the Microsoft Windows
operating system was the offender. Microsoft was quick to acknowledge the problem, stating the
issue affected machines running the CrowdStrike Falcon product.
There is still much unknown about the botched CrowdStrike software update. The company was
quick to announce the outage was not a result of a cyberattack. Industry experts widely
believe the offending software update was not digitally signed and had not undergone adequate
testing.
The sheer extent of the crash necessitates a close inspection of processes and procedures of
deploying software updates. If there’s one lesson to be learned from the CrowdStrike outage,
it’s this: Code signing must be an integral part of an organization’s software development
lifecycle.
Code signing is a security technology used to certify the authenticity and integrity of
software code. When developers release an update or software patch, they digitally sign the
code using a private key. This signature can then be verified by end-users using the
corresponding public key.
While there’s no indication at this time that the CrowdStrike update was tampered with, by not
signing the code that caused a massive global outage, CrowdStrike certainly lost considerable
trust. A code signing solution could have played a crucial role in mitigating the impact of
the flawed update. Code signing ensures that software updates have not been tampered with or
altered since it was signed by the developer. If the problematic CrowdStrike update had been
compromised or corrupted during transmission or deployment, code signing verification would
have detected these unauthorized changes. This detection could have prevented the flawed
update from being applied, adding a critical layer of trust. Without digital signature
verification there is no ability for the community to know without a shadow of doubt that a
malicious actor was not impersonating a legitimate update from CrowdStrike. For a
cybersecurity company whose brand relies on trust and legitimacy this is not a good
look.
Zeva’s Chief Technology Officer, Mr. Gary DiPalma added, “Code signing has become an integral
part of DevSecOps. It is imperative that organizations ensure the provenance of their source
code and artifacts. Using non-reputable and trusted digital signatures on source code, audit
logs, and software builds that are integrated within the DevSecOps process, can address and
validate their software bill of materials.
While code signing is not a panacea, it is a vital component of a comprehensive security
strategy. It offers a proactive measure to detect and block unauthorized or corrupted software
before it causes widespread issues. Given the interconnected nature of modern IT
infrastructures, implementing robust code signing practices is essential to build resilience
against similar disruptions in the future.
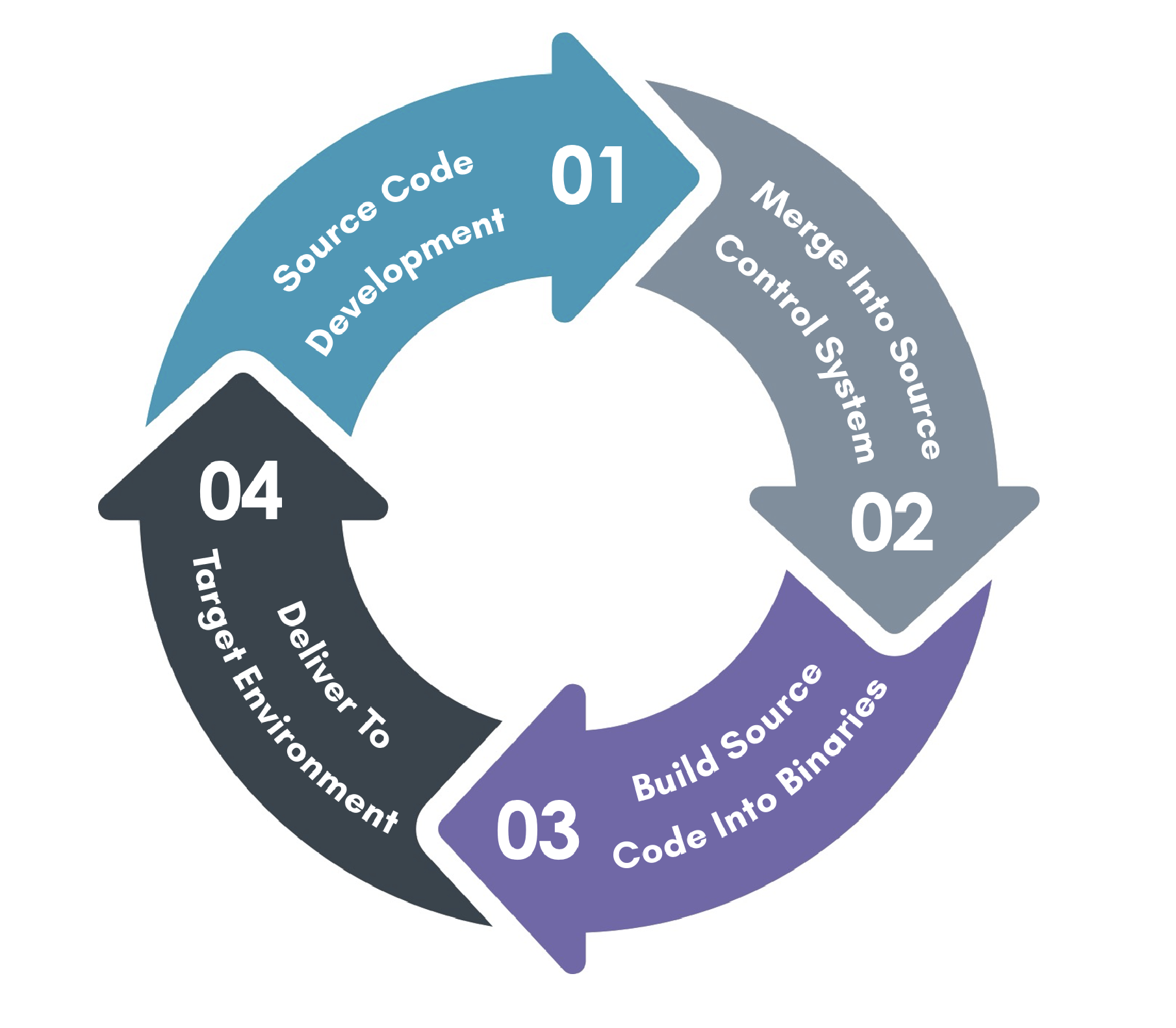
Zeva’s CodeLocker product allows companies to achieve end-to-end software governance. The
product is an automated, customizable, and trusted code-signing solution.
“CodeLocker is a software provenance product that starts with signing the developer’s source
code, signing during the review, approval, and commit process, and finishing with signing the
build/container for deployment. This achieves End-to-End integrity and traceability of the
Software Provenance Life Cycle,” stated DiPalma.
To learn more about Zeva’s CodeLocker and watch a demo visit CodeLocker.zevainc.com














